Anomaly detection is critical to running a successful FinOps practice. In this comparison blog, we’ll look at anomaly detection functionality in AWS, Microsoft Azure, and Google Cloud native tools. You can use these tools if you do not currently have a dedicated cloud cost management or FinOps platform. We’ll also discuss the scenarios in which it makes sense to implement customization options in your anomaly detection.
Anomaly detection in AWS
In December 2020, AWS Cost Explorer began providing a service called Cost Anomaly Detection. Since then, AWS has implemented several updates (detailed in its documentation). The latest Cost Explorer release, in November 2024, helps you analyze potential root causes of each anomaly.
(Important note: If you use AWS as a standalone or management account, and if you enabled AWS Cost Explorer on or after March 27, 2023, Cost Anomaly Detection is active by default. If you enabled AWS Cost Explorer before that date, you’ll need to manually activate Cost Anomaly Detection in the Cost Explorer console. There are some limitations, too, in the number of monitors and subscriptions that you can access using AWS Cost Anomaly Detection.)
AWS cost monitors
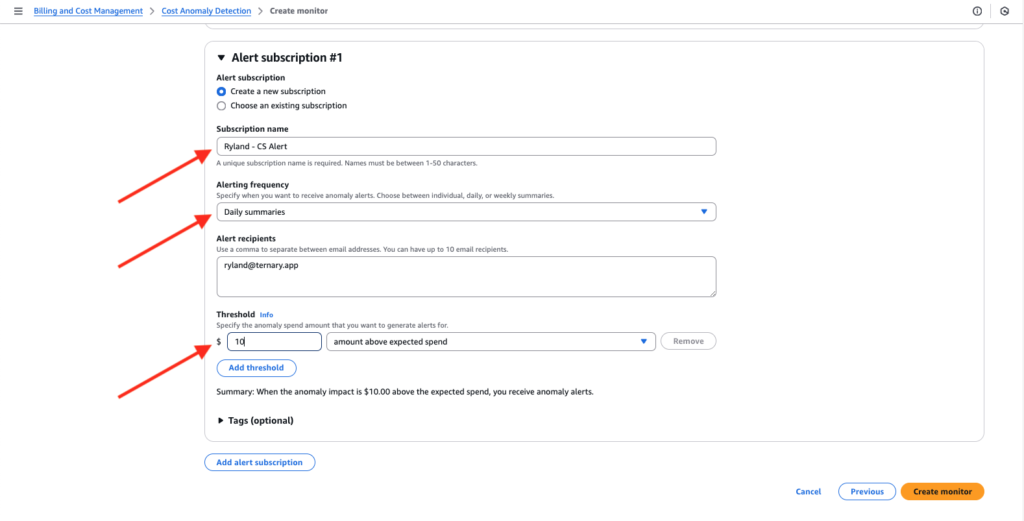
A cost monitor is an automated tool that compares your forecasted usage with actual usage. You receive an alert in the event of surges that exceed your designated level. Read more about creating a cost monitor in AWS.
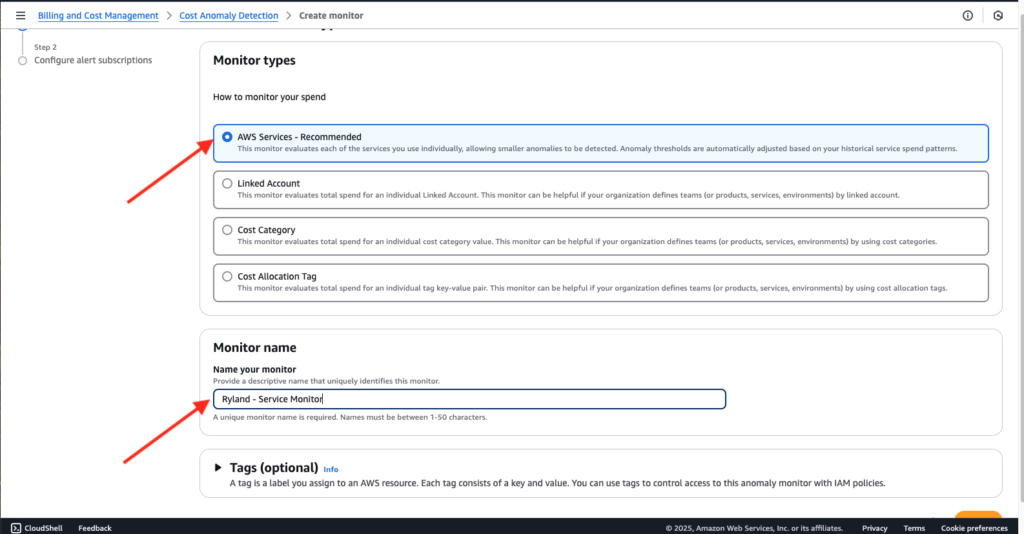
There are several options for AWS cost monitors, each detecting anomalies in a different way. These options include AWS Services (which limits users to one monitor per account); Linked Account; Cost Category (which is best for organizations that explicitly define cost categories in AWS); or Cost Allocation Tag (key-value pairs you have enabled in your AWS Cost and Usage Report).
AWS does more than provide anomaly alerts in the Cost Explorer console. It also allows you to retrieve them using an API, leveraging your existing workflows.
It’s important to note that AWS does not support anomaly alerts in some of its services (e.g., AWS Marketplace, AWS Support, WorkSpaces, Cost Explorer, Budgets, AWS Shield, Amazon Route 53, and AWS Certificate Manager, as well as upfront and recurring reserved fee and Savings Plan fees). This gap in visibility could allow unplanned spending to continue unchecked.
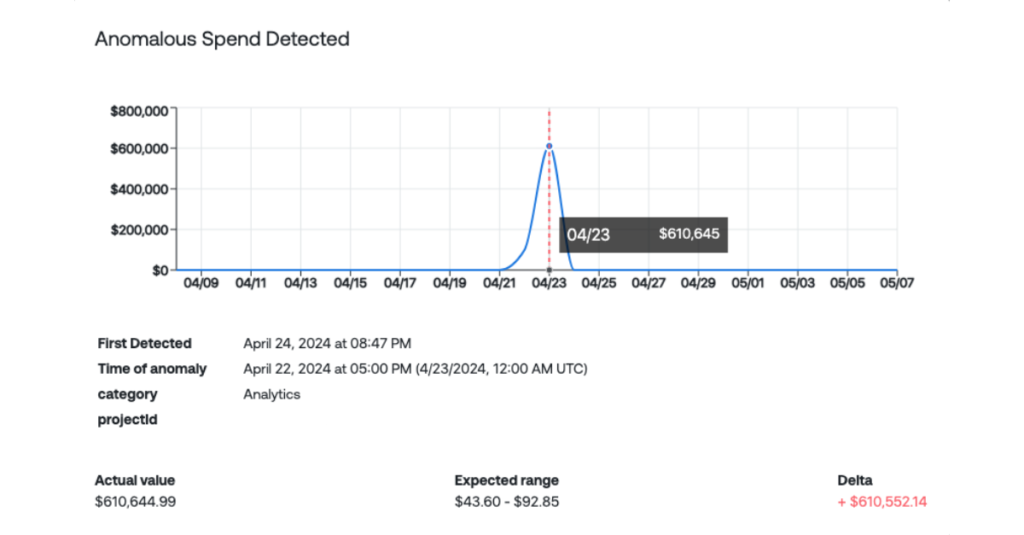
In those services for which AWS does provide anomaly detection, you must simply create a cost monitor in order to activate alerts. The “Detected anomalies” tab on the Cost Anomaly Detection page will display an alert with the following details:
- Start date (what day the anomaly was first detected)
- Last detected (the last time anomaly was detected)
- Duration (how long the anomaly lasted; if the anomaly is ongoing, the alert notes this)
- Cost impact (how much spending increased, compared with expected spend)
- Impact percentage (total cost impact/expected spend)
- Name of anomaly monitor
- Top root cause (service) (top service root cause for the anomaly)
- Account (which account ID and name caused the anomaly)
- Region
- Usage type
- Expected spend
- Actual spend
- Assessment (an option for the user to share feedback for improving the ML model)
- Severity (how abnormal a certain anomaly is, accounting for historical spending patterns; generally, the higher the severity, the larger the spike)
Anomaly detection in Azure
Similar to AWS, Azure has built-in functionality for anomaly detection, using an ML algorithm, WaveNet, to model divergences from expected spending. You can access this functionality through the Microsoft Cost Management page in the Azure portal. (Note: Anomaly detection is not enabled by default; you must manually enable it for each subscription to receive anomaly detection notifications by email.)
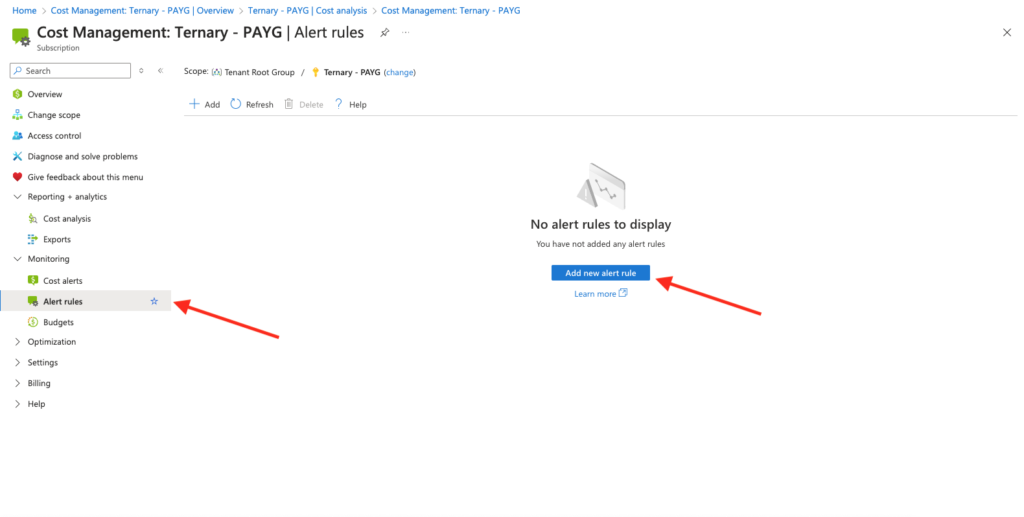
Once you navigate to Microsoft Cost Management in the Azure portal, you can select “Cost analysis,” and select any view under “Smart views” (e.g., Resources, Reservations, Services). If you have a cost anomaly, you will see an “Insight” related to that anomaly.
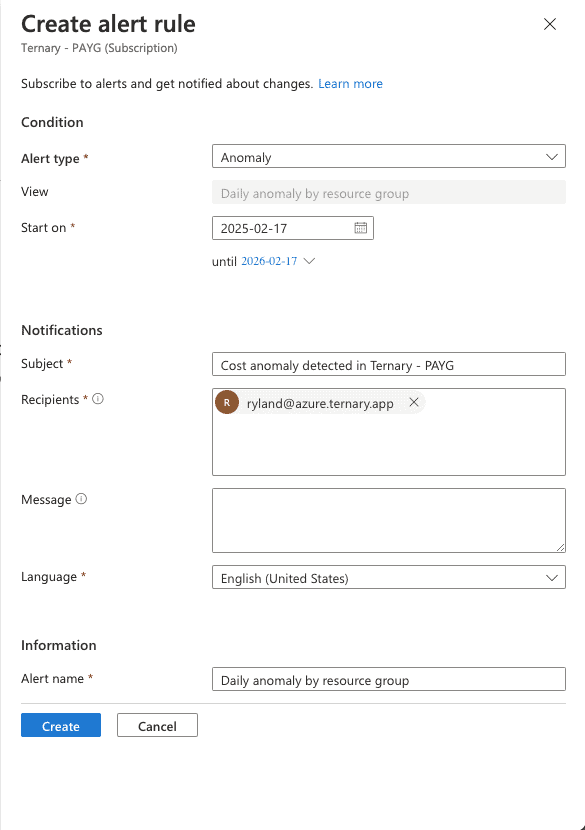
Azure offers less flexibility than AWS. For example, in the alert rule, you can’t specify the scope of the alert or set any thresholds. (You also can’t specify the dollar amount or the percentage over or under an expected range of spend for services, tags, etc.) Instead, you simply select the subscription you want to create an anomaly alert rule for. Once you’ve done this, the anomaly alert will compile a summary of changes, sorted by resource group count and cost.
Unlike AWS, Microsoft does not appear to provide an API to access your cost anomaly alerts. That means you can’t integrate anomaly detection within your existing workflows.
Anomaly detection in Google Cloud
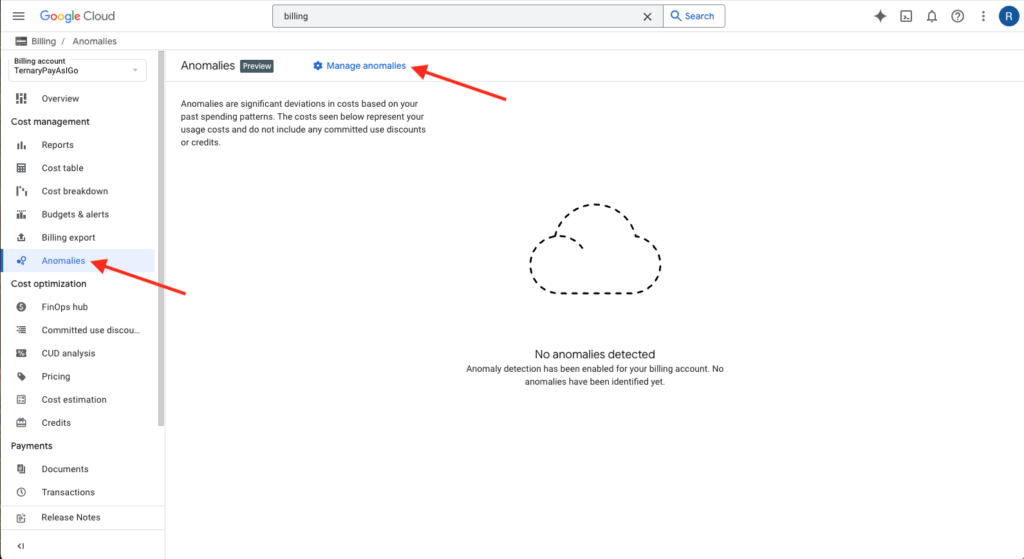
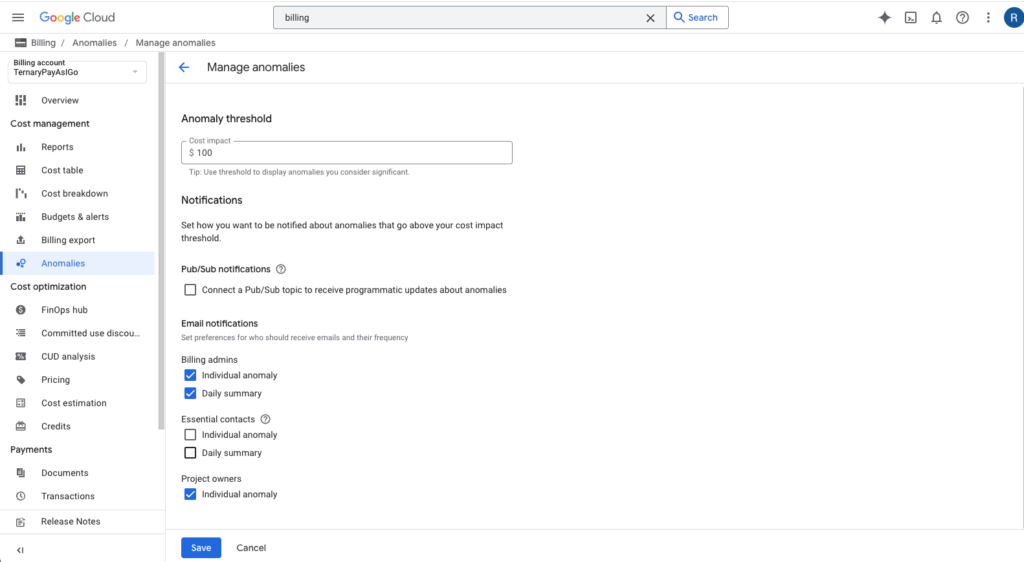
Google Cloud (GCP) also offers native cost anomaly detection. But unlike AWS or Azure, GCP enables anomaly detection (at the project level) by default. There’s no need to manually activate it. GCP leverages an AI model to identify your spend patterns based on historical and seasonal trends specific to your project. It monitors your actual spend every hour, detecting any deviation.
Like Azure, GCP offers relatively little ability to filter or scope anomaly alerts. But unlike Azure, GCP does allow you to set a spending threshold that, once surpassed, triggers an anomaly alert. Other than that, GCP offers customizability only with regard to who receives alert notifications and how (e.g., Pub/Sub or email).
Level up your anomaly detection with Ternary
As you can see, each of the three major cloud service providers (CSPs) offers its own version of anomaly detection. For some use cases, one or more of these native tools may be sufficient.
But a key aspect of managing anomaly alerts effectively is reducing false positives (“noise”). This requires a level of data analysis that may not be available using native tools. Plus, some users may wish to create more granular, targeted alerts. Others may want to see their anomalies across all CSPs. Ternary can help with these efforts, by offering greater customization and deeper analysis.
Consider this hypothetical scenario: You want to create anomaly alerts specific to each of your five teams. It’s unlikely that you could do this using native tools. But in Ternary, you could leverage existing tags/labels or Ternary Custom Labels to create highly targeted anomalies for each team.
Let’s look at another example. If you use AWS, Azure, and GCP, you may want to understand what your “expected” spend is across Amazon Elastic Compute Cloud (EC2) Instances, Azure Virtual Machines, and Google Compute Engine Virtual Machines for any given day. With native solutions, each of these services would be siloed. But with Ternary Anomaly Detection, you can draw connections, by creating a new rule, filtering the data to that product’s Custom Label, and sub-filtering to look only at EC2 spend.
Ternary allows you to aggregate spend across multiple cloud vendors and to create targeted alerts that native solutions can’t offer. Plus, if your organization uses other service providers (such as MongoDB or Snowflake), Ternary can help you create anomaly alerts aggregated across all of your clouds. Ternary’s ML-powered platform helps you stay on top of spikes while reducing cumbersome manual analysis.
We hope you’ve found this discussion helpful for detecting anomalies using each of the three major CSPs.
Unlock the power of multi-cloud anomaly detection.